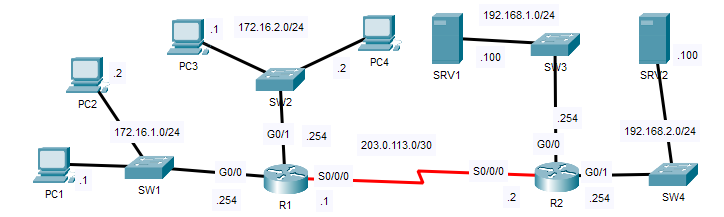
Configure OSPF on R1 and R2 to allow full connectivity between the PCs and servers.
Configure standard numbered ACLS on R1 and standard named ACLs on R2
to fulfill the following network policies:
-Only PC1 and PC3 can access 192.168.1.0/24
-Hosts in 172.16.2.0/24 can’t access 192.168.2.0/24
-172.16.1.0/24 can’t access 172.16.2.0/24
-172.16.2.0/24 can’t access 172.16.1.0/24
1. Configure OSPF on R1 and R2 to allow full connectivity between the PCs and servers.
Enabled R1’s G0/0, G0/1, and S0/0/0, and confirmed their status.
1 | R1> |
The same is done for R2. OSPF is enabled on all interfaces.
1 | R2(config)#router ospf 1 |
We can check if R2 has established a connection with R1, as well as identify routes created by OSPF.
1 | R2(config-router)#do sh ip ospf neigh |
We can verify the routes here from R2 to R1 via the S0/0/0 interface.
1 | O 172.16.1.0/24 [110/65] via 203.0.113.1, 00:00:55, Serial0/0/0 |
R1’s route are also dynamically added via OSPF as shown.
1 | R1(config-router)#do sh ip route |
We have full connectivity in the network.
2. Configure standard numbered ACLS on R1 and standard named ACLs on R2
to fulfill the following network policies:
-Only PC1 and PC3 can access 192.168.1.0/24
-Hosts in 172.16.2.0/24 can't access 192.168.2.0/24
-172.16.1.0/24 can't access 172.16.2.0/24
-172.16.2.0/24 can't access 172.16.1.0/24
To fulfill requirements 1.
-Only PC1 and PC3 can access 192.168.1.0/24
The standard for ACL named mode is as follows:
1 | R2(config)#ip access-list standard ? |
We applied the ACL to g0/0 outbound.
We can verify PC1 can reach SRV1.
1 | C:\>ping 192.168.1.100 |
PC2 cannot reach SRV1 as per the ACL.
1 | Pinging 192.168.1.100 with 32 bytes of data: |
To fulfill requirement 2:
-Hosts in 172.16.2.0/24 can’t access 192.168.2.0/24
1 | R2(config)#ip a |
Note that the permit any is required here to allow other traffic through.
We can see the full ACLs here:
1 | R2(config-if)#do sh access-list |
To meet requirement 3 and 4:
-172.16.1.0/24 can’t access 172.16.2.0/24
-172.16.2.0/24 can’t access 172.16.1.0/24
We will use access-list here.
1 | R1(config)#access-list 1 deny 172.16.1.0 0.0.0.255 |