allow all traffic
1
R1(config-ext-nacl)#permit ip any any
prevent 10.0.0.16 from sending udp traffic to 192.168.1.1/32
1
R1(config-ext-nacl)#deny udp 10.0.0.16 0.0.0.0 host 192.168.1.1
prevent 127.0.0.1/32 from pinging hosts in 192.168.0.1/24
1
R1(config-ext-nacl)#deny icmp host 127.0.0.1 192.168.0.0 0.0.0.255
Allow traffic from 10.0.0.0/16 to access the server at 2.2.2.2 using https.
1
R1(config-ext-nacl)#permit tcp 10.0.0.0 0.0.255.255 2.2.2.2 0.0.0.0 eq 443
Prevent all hosts using source udp port numbers from 20000 to 30000 from accessing the server at 3.3.3.32.
1 | R1(config-ext-nacl)#deny udp any range 20000 30000 host 3.3.3.3 |
- Allow hosts in 172.16.1.0/24 using a TCP source port greater than 9999 to access all TCP ports on server 4.4.4.4 except port 23.
1 | R1(config-ext-nacl)#permit tcp 172.16.1.0 0.0.0.255 gt 9999 host 4.4.4.4 neq 23 |
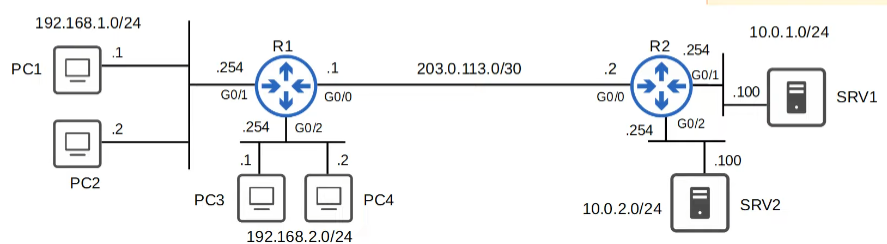
Requirements:
- Hosts in 192.168.1.0/24 can’t use HTTPS to access SRV1.
- Hosts in 192.168.2.0/24 can’t access 10.0.2.0/24.
- None of the hosts in 192.168.1.0/24 or 192.168.2.0/24 can ping 10.0.1.0/24 or 10.0.2.0/24.
Hosts in 192.168.1.0/24 can’t use HTTPS to access SRV1.
1 | R1(config)#ip access-list extended HTTP_SRV1 |
Hosts in 192.168.2.0/24 can’t access 10.0.2.0/24.
1 | R1(config)#ip access-list extended BLOCK_10.0.2.0/24 |
None of the hosts in 192.168.1.0/24 or 192.168.2.0/24 can ping 10.0.1.0/24 or 10.0.2.0/24.
1 | R1(config)#ip access-list extended BLOCK_PING_SRV1_SRV2 |
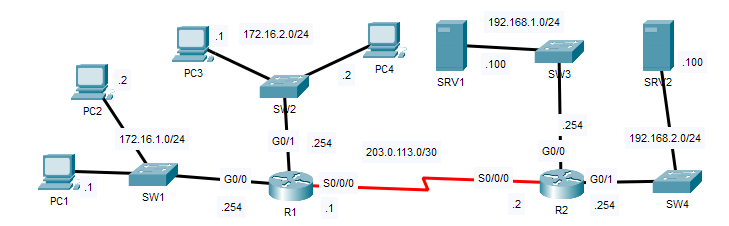
- Configure extended ACLS to fulfill the following network policies:
-Hosts in 172.16.2.0/24 can’t communicate with PC1.
-Hosts in 172.16.1.0/24 can’t access the DNS service on SRV1.
-Hosts in 172.16.2.0/24 can’t access the HTTP or HTTPS services on SRV2.
1st and 3rd Requirement:
1 | R1(config)#ip access-list extended 101 |
2nd requirement: Hosts in 172.16.1.0/24 can’t access the DNS service on SRV1.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21R1(config)#ip access-list extended 100
R1(config-ext-nacl)#deny udp 172.16.1.0 0.0.0.255 host 192.168.1.100 eq 53
R1(config-ext-nacl)#deny tcp 172.16.1.0 0.0.0.255 host 192.168.1.100 eq 53
R1(config-ext-nacl)#permit ip any any
R1(config-ext-nacl)#exit
R1(config)#int g0/0
R1(config-if)#ip ?
access-group Specify access control for packets
address Set the IP address of an interface
authentication authentication subcommands
flow NetFlow Related commands
hello-interval Configures IP-EIGRP hello interval
helper-address Specify a destination address for UDP broadcasts
mtu Set IP Maximum Transmission Unit
nat NAT interface commands
ospf OSPF interface commands
proxy-arp Enable proxy ARP
split-horizon Perform split horizon
summary-address Perform address summarization
R1(config-if)#ip access-group 100 in
R1(config-if)#
1 | R1#show access-lists |